Is Pam Bondi Married To Greg Henderson? Exploring The Search And Related Information
It's quite natural, actually, to be curious about the personal lives of public figures, and searches like "is Pam Bondi married to Greg Henderson" pop up quite a bit. People, you know, often wonder about the relationships and family details of individuals who are in the public eye. This particular question, it seems, has piqued a good many people's interest lately, leading them to search for answers online.
When someone types a question like this into a search engine, they're typically looking for clear, straightforward information. They want to know the facts, more or less, about a person's marital status and who they might be linked to. It's a very human desire to connect with and understand the lives of others, especially those we see in news or public roles.
However, the name "Pam" can, in a way, lead to a little confusion. While many might think of a specific person, "Pam" also shows up in other important contexts, like in the world of cybersecurity or even healthcare. We'll explore the common search query about Pam Bondi and Greg Henderson, and then, too, we'll look at some other "Pams" that might just be part of the information you're really looking for, especially when we consider topics like Privileged Access Management (PAM) or even individuals like Pamela Lewis, an OB/GYN, as mentioned in our background information.
Table of Contents
- Unpacking the "Is Pam Bondi Married to Greg Henderson" Query
- Who is Pam Bondi?
- Exploring Other "Pams" and What Your Search Might Uncover
- Frequently Asked Questions
- Final Thoughts on "Is Pam Bondi Married to Greg Henderson"
Unpacking the "Is Pam Bondi Married to Greg Henderson" Query
When someone types "is Pam Bondi married to Greg Henderson" into a search bar, they're typically looking for very specific details about a public figure's personal life. Pam Bondi, you know, is a well-known name in American politics, having served as Florida's Attorney General. Her public role often brings her personal life into the spotlight, so it's not surprising that people would be curious about her relationships. As of today, April 29, 2024, public records and widely available information do not indicate that Pam Bondi is married to a Greg Henderson. It's a query that comes up, perhaps, from some confusion or a simple curiosity about her current status.
It's important to remember that public figures, too, have a right to privacy, though some aspects of their lives become public knowledge. Pam Bondi has, in fact, been married previously, but her marital history does not include a marriage to someone named Greg Henderson, at least not according to publicly verifiable sources. This search query, then, might be based on a misunderstanding or a simple desire to confirm a piece of information that isn't, in fact, accurate.
Searches like this, you know, often highlight how much we rely on quick answers. Sometimes, the information we're looking for just isn't out there in the way we expect, or it might be a mix-up of names or details. It's a good reminder to always look for credible sources when trying to confirm personal information about anyone, especially those in the public eye. So, to be clear, based on publicly available and widely reported information, Pam Bondi is not married to Greg Henderson.
Who is Pam Bondi?
Pam Bondi, for those who might not be completely familiar, is a rather prominent American attorney and politician. She served as the Attorney General of Florida from 2011 to 2019. During her time in office, she was involved in many high-profile cases and policy decisions, which, naturally, kept her in the public eye quite a bit. Her career has, in a way, been marked by her strong presence and her work on various legal matters affecting the state of Florida.
After her tenure as Attorney General, she continued to be a visible figure, often appearing on television as a legal analyst and, too, playing a role in various political campaigns and administrations. Her career path shows a consistent involvement in law and public service. While her professional life is widely documented, details about her personal life, like her marital status, tend to be less formally publicized, unless, of course, they become part of a public record.
So, when people search for her personal details, it's usually because they've seen her in a professional capacity and are simply curious about the person behind the public persona. It's a very common thing, you know, for people to want to know more about the lives of individuals they see on the news or in government. But, as we've said, the specific query about Greg Henderson does not align with publicly confirmed facts about her marital history.
Exploring Other "Pams" and What Your Search Might Uncover
It's interesting how a simple name like "Pam" can lead down so many different paths, isn't it? While many folks might be looking for information about Pam Bondi, the former Florida Attorney General, the term "Pam" also holds significant meaning in other important areas, especially in technology and healthcare. This is where our background information, the "My text" you provided, really comes into play. It talks about a couple of very different "Pams," which could, in some respects, be what someone is actually looking for, or at least, it shows how broad a single name can be.
Sometimes, too, a search query might unintentionally lead to related but distinct topics. We're going to explore two other "Pams" that are quite different from Pam Bondi, but are equally important in their own fields. This shows just how varied the information linked to a simple name can be, and why it's good to be specific when you're looking for something. It's almost like, you know, searching for "apple" and finding both fruit and a tech company.
Privileged Access Management (PAM): A Different Kind of "Pam"
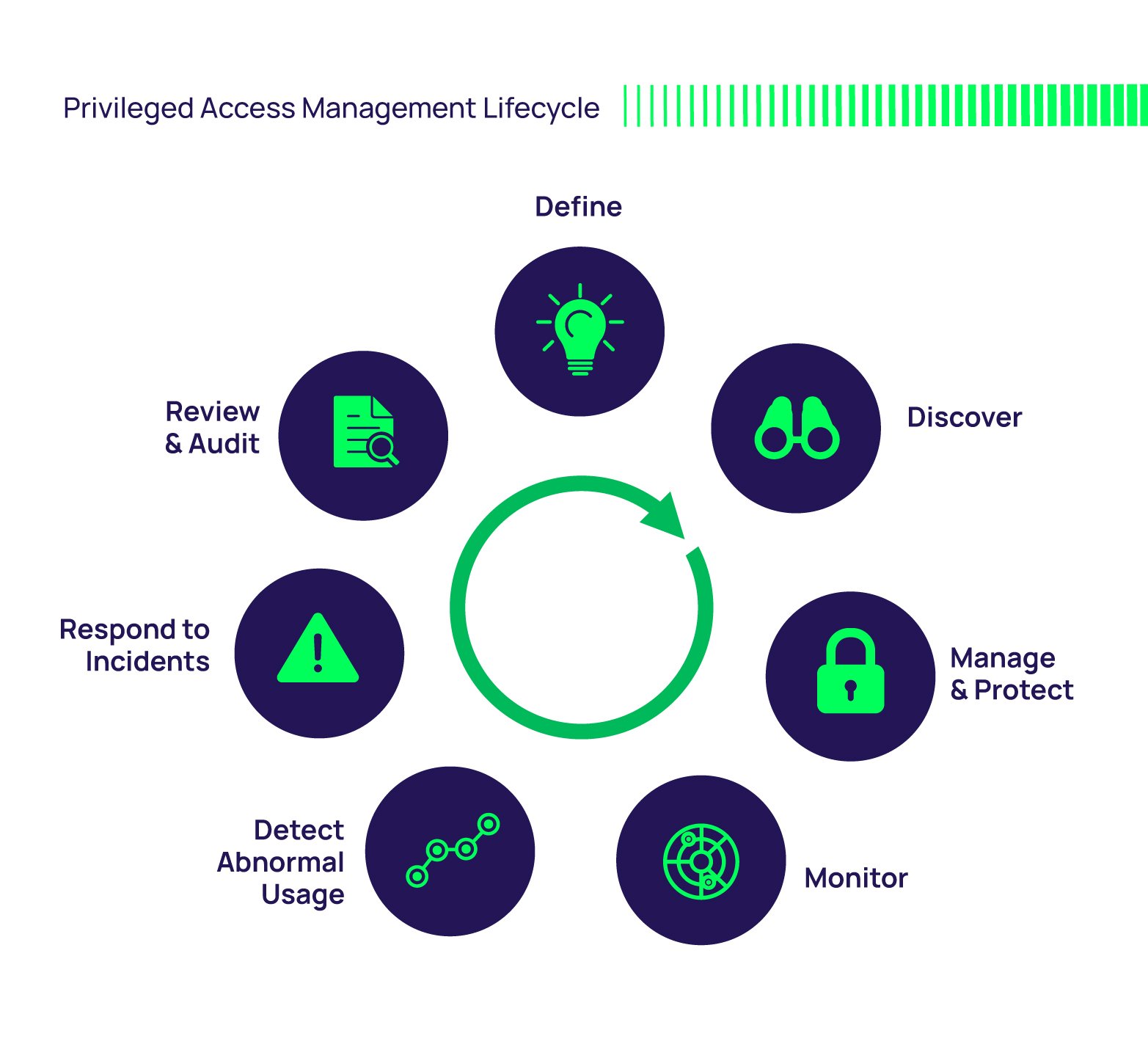
One of the most significant "Pams" that might pop up in a different context, particularly for businesses and anyone interested in digital security, is Privileged Access Management, or PAM. This isn't a person at all, but rather a very important cybersecurity strategy. It's basically a set of tools and practices that help organizations keep their most sensitive digital assets safe. Think of it like a very, very strict security guard for the most important keys and doors in a digital building. This system is crucial today, as cyberthreats are, in fact, always changing and getting more complex.
Privileged Access Management (PAM) is an identity security solution that helps protect organizations against cyberthreats by monitoring, detecting, and preventing unauthorized privileged access to critical resources. So, if you're searching for "Pam" and happen to be in the IT world, this might be the "Pam" you're thinking of. It's all about making sure that only the right people, and only when absolutely necessary, can get into the most sensitive parts of a computer system. This is, you know, a very big deal for keeping data safe.
PAM consists of cybersecurity strategies and technologies for exerting control over the elevated (“privileged”) access and permissions for identities, users, accounts, processes, and systems across an IT environment. It's a rather comprehensive approach, really, designed to give organizations a firm grip on who can do what with their most valuable digital information. This control is vital for preventing data breaches and other security incidents, which can, in fact, be incredibly damaging to a business. It's a system that requires careful planning and, too, constant oversight.
The Essence of PAM: What It Is and Why It Matters
At its core, Privileged Access Management is a type of identity management and a branch of cybersecurity that focuses on the control, monitoring, and protection of privileged accounts within an organization. These "privileged accounts" are like the master keys to a system; they have extensive permissions and can, therefore, make big changes or access highly sensitive data. Think of system administrators, database managers, or even automated processes that need elevated access to function. Without proper PAM, these accounts could be, you know, a huge weak spot for attackers.
The importance of PAM cannot be overstated in today's digital world. Cyberattacks are, unfortunately, a constant threat, and often, attackers try to get hold of these privileged accounts because they offer the quickest path to an organization's most valuable assets. By managing and securing these accounts, PAM helps organizations significantly reduce their risk of a breach. It's about being proactive rather than reactive when it comes to security, which, as a matter of fact, saves a lot of headaches later on.
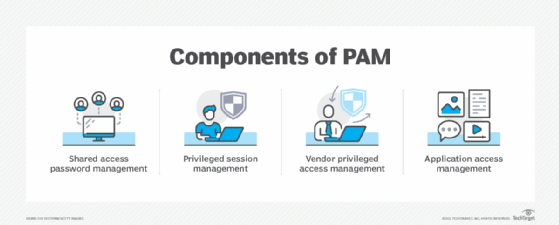
PAM works through a combination of people, processes, and technology that enables organizations to safeguard their critical assets by enforcing strict controls on who can access privileged accounts and how they can use them. It's not just about software; it's also about having clear rules and trained staff who understand the importance of these controls. This holistic approach means that security is built into every layer, making it much harder for unauthorized individuals to slip through the cracks. It's a pretty robust system, really, when implemented correctly.
How PAM Works: A Closer Look at Protection
So, how does this digital guardian, PAM, actually operate? Basically, PAM solutions typically involve several key components. One aspect is managing credentials for privileged accounts, often by storing them in a secure, encrypted vault. This prevents individuals from knowing the actual passwords, which, you know, reduces the risk of them being stolen or misused. Instead, users request access through the PAM system, which then grants temporary, just-in-time access to the necessary resources.
Another crucial part is session monitoring. This means that every action taken by a user with privileged access is recorded and monitored. If something looks suspicious, the system can, in fact, flag it or even terminate the session. This level of oversight provides an audit trail, which is incredibly valuable for compliance and for investigating any security incidents that might occur. It's like having a security camera on every single privileged action, which is, you know, a very good thing for accountability.
Furthermore, PAM systems often include features like multi-factor authentication for privileged access, ensuring that even if a password is compromised, an additional layer of verification is needed. They also enforce least privilege principles, meaning users are only given the minimum level of access required to perform their specific tasks, and for the shortest possible time. This dramatically limits the potential damage if an account is, by chance, compromised. It's all about minimizing risk, which, you know, is a really smart way to handle security.
PAM as a Branch of Cybersecurity: Controlling Access
Privileged Access Management, or PAM, safeguards access to sensitive systems and data by controlling privileged accounts. It's a very specialized area within the broader field of cybersecurity, but it’s one that’s getting more and more attention because of its critical role in protecting an organization’s most valuable information. Without strong PAM, even the most advanced firewalls or antivirus software might not be enough to stop a determined attacker who gains control of a privileged account. It’s a bit like having a strong front door but leaving the back door wide open, you know?
The focus here is specifically on those accounts that have "elevated" permissions – the ones that can install software, change system configurations, access all user data, or manage other accounts. These are the crown jewels of any IT environment, and so, they need the highest level of protection. PAM provides that by implementing very strict policies around their use. It's not just about stopping external threats, either; it's also about preventing misuse or accidental errors by internal staff who have these powerful permissions. That, too, is a big part of why it's so important.
PAM is a cybersecurity strategy and set of technologies aimed at safeguarding an organization’s most sensitive data and critical systems by meticulously controlling access. This means that every single time someone or something tries to use a privileged account, the PAM system is there to verify, monitor, and record that activity. This constant oversight helps to quickly identify and respond to any unauthorized attempts or suspicious behavior, which, you know, is pretty much what you want in a security system. It's a continuous process, not a one-time setup.
Safeguarding Sensitive Data with PAM
When we talk about protecting an organization’s most sensitive data, PAM is, frankly, at the forefront. This includes everything from customer financial records and intellectual property to internal strategic documents and employee information. If privileged accounts are compromised, all of this valuable data could be stolen, altered, or destroyed, leading to massive financial losses, reputational damage, and legal consequences. PAM is, therefore, a very important line of defense against these kinds of catastrophic events.
The system helps to enforce regulatory compliance, too, which is a big deal for many industries. Laws like GDPR, HIPAA, and various financial regulations often require organizations to demonstrate stringent controls over who can access sensitive data. PAM provides the tools and audit trails necessary to meet these strict requirements, which can, in fact, prevent hefty fines and legal issues. It's not just good security practice; it's often a legal necessity, you know, to have these systems in place.
Ultimately, PAM gives organizations peace of mind by significantly reducing the attack surface related to privileged accounts. It ensures that critical assets are protected, and that access is granted only to those who truly need it, for the right reasons, and at the right time. This kind of careful management is, you know, essential for any organization that wants to thrive securely in the digital age. It’s a pretty smart investment, really, for any business that values its data.
Pamela Lewis: Another "Pam" in Focus
Moving from the technical "PAM" back to people, our background information also mentions Pamela Lewis, who is, in fact, an OB/GYN at Louisiana Women’s Healthcare in Baton Rouge, Louisiana. This is another "Pam" that your search might, in a way, have inadvertently touched upon, or at least, it shows the diversity of individuals named Pam who are doing important work. She represents a completely different field from politics or cybersecurity, focusing on healthcare and patient well-being.
Pamela Lewis's journey into medicine is quite impressive. She is a native of St. Francisville, Louisiana, and graduated from West Feliciana High School as valedictorian. She then completed her undergraduate studies from the University of Louisiana at Monroe, graduating magna cum laude. She earned her medical doctorate from Louisiana State University (LSU) Health Sciences Center in New Orleans. Her dedication to her education and her field is, you know, very clear from her academic achievements.
Her work as an OB/GYN is a vital service, providing care and support to women in her community. This "Pam" is focused on providing patients with the best care and outcomes, which is a truly noble profession. It just goes to show that a name can, you know, lead to many different stories and professional paths. It's a good reminder that not every "Pam" is the same, and each one has their own unique contributions.
| Detail | Information |
|---|---|
| Profession | OB/GYN (Obstetrician/Gynecologist) |
| Current Practice | Louisiana Women’s Healthcare, Baton Rouge, Louisiana |
| Hometown | St. Francisville, Louisiana |
| High School | West Feliciana High School (Valedictorian) |
| Undergraduate | University of Louisiana at Monroe (Magna Cum Laude) |
| Medical School | Louisiana State University (LSU) Health Sciences Center, New Orleans |
Frequently Asked Questions
Is Pam Bondi currently married?
Based on publicly available information as of today, April 29, 2024, Pam Bondi is not currently married. She has been married previously, but her current status is understood to be single. It's always a good idea, you know, to check reliable news sources for the most up-to-date personal information about public figures.
Who is Pam Bondi's husband?
Pam Bondi has had two previous marriages. Her first marriage was to Garret Barnes, and her second was to John T. Lewis. However, as noted, there is no public record or widely reported information indicating that she has ever been married to a Greg Henderson. So, to be clear, Greg Henderson is not, in fact, Pam Bondi's husband.
What is Privileged Access Management (PAM)?
Privileged Access Management (PAM) is a cybersecurity solution designed to protect organizations from cyberthreats. It does this by controlling, monitoring, and securing access to highly sensitive accounts and systems within an IT environment. PAM ensures that only authorized individuals or processes can use "privileged" accounts, which, you know, have extensive permissions. It's a very important part of keeping digital data safe and secure. You can learn more about cybersecurity best practices on government sites.
Final Thoughts on "Is Pam Bondi Married to Greg Henderson"
So, when you type "is Pam Bondi married to Greg Henderson" into a search engine, you're, you know, looking for a very specific piece of information. As we've seen, based on publicly available records, Pam Bondi is not married to Greg Henderson. It's a straightforward answer to a direct question, really, and it helps clear up any possible confusion that might be out there. It’s important to rely on verified sources for such details.
This journey through the various "Pams" also highlights something pretty interesting about how information is organized and searched for online. A simple name can lead to very different topics, from the
What is Privileged Access Management (PAM)? | Delinea

Conoce nuestro aceite de canola comestible en spray | PAM®
What is privileged access management (PAM)? (2022)